What is Bitcoin?
A serious deep dive into what Bitcoin is and how it works to provide a secure and decentralized global transaction network.
Introduction
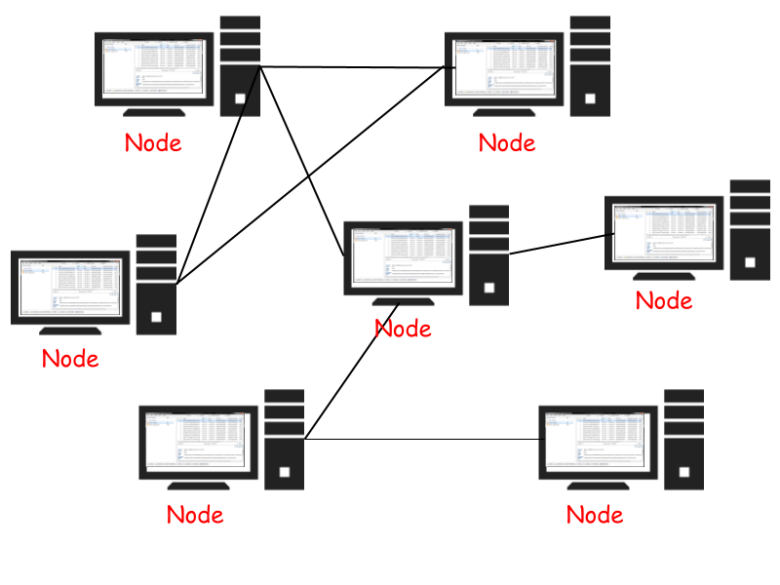
Bitcoin is a digital file which lists accounts and their balances in a public ledger. A copy of the ledger is maintained by every node on the network. A node is a computer which is participating in the Bitcoin public consensus protocol, and there are tens or hundreds of thousands of them online today.
Bitcoin is not backed by any physical commodity like gold standard currencies, but unlike fiat currencies Bitcoin has limited supply and requires energy to create. Therefore, it does not suffer from inflation like what we see with modern centralized money printing, and have seen historically during the decline of the Roman Empire and other fallen civilizations.
To make a transaction, a user broadcasts to the network that the balance on their account should go down, and the receiver´s account should go up. Nodes then apply that transaction to their copy of the ledger and pass the data on to other nodes. Since the transaction information is distributed through a decentralized network of peers, there is no central authority to control or limit transactions. Security is upheld harmoniously by Bitcoin users themselves.
This already sounds quite different to traditional banking. Elaborating on what sets them apart, by the nature of how Bitcoin has succeeded in decentralization, all transactions are public information. Furthermore, while a bank is a legal entity which manages their clients´ wealth and mediates in cases of fraud or mistakes, on the Bitcoin network the vast majority of users are completely anonymous and there is no customer support to save the day if things go wrong. This is what inspired the most popular Bitcoin mantra of all:
“Don´t trust, verify.” - Steven D. Levitt
Bitcoin is ingeniously designed so that no trust is required. Special mathmatical functions protect every aspect of the system, and down to the open-source code itself, everything about Bitcoin is verifiable to those with sufficient curiosity, understanding, and discernment.
Under the hood
Let us go on a deep dive into how Bitcoin enables a group of trustless strangers to securely handle each other´s financial transactions with no central authority, complete autonomy, and on a global scale.
Sending Money & Authentication
At a basic level, for Peter to send bitcoin to Paul, he broadcasts a message to the network with the accounts and the amount. “Send X bitcoin from Peter to Paul.” Every node which receives the message from Peter updates their copy of their public ledger, and relays the message to more nodes on the network who also update and pass on the message. But how can the network know that the transaction is authentic?
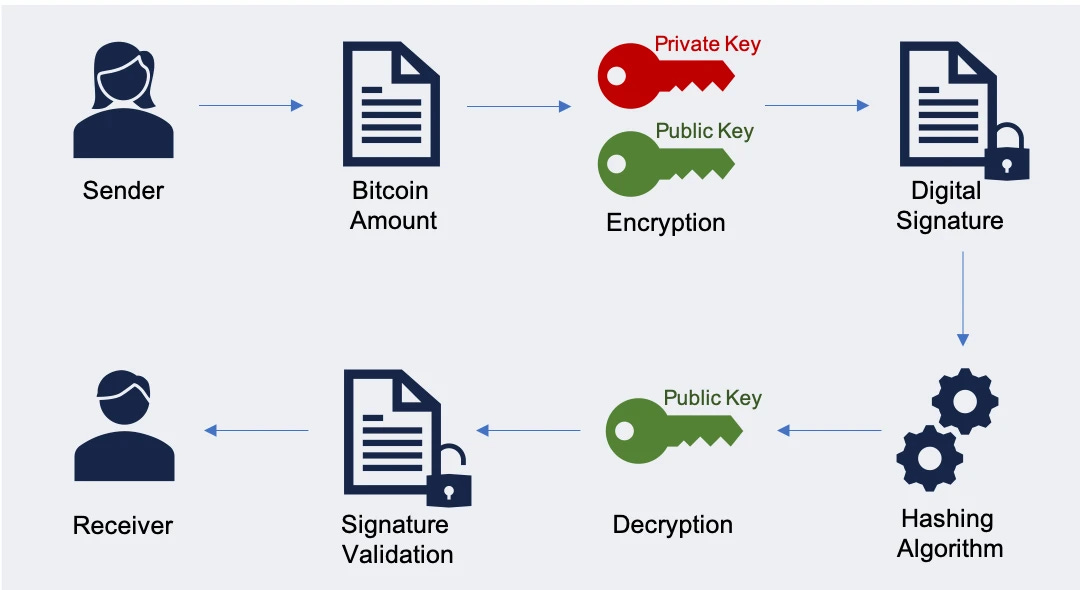
Moving money out of a Bitcoin account requires a special password, known as a digital signature, which proves the authenticity of the transaction. Unlike a static password, a different digital signature is required for every transaction a user makes. This protects the user´s account from hackers and thieves.
Digital signatures for Bitcoin transactions are created by a private key, and verified with a public key. The private key is the true password, and digital signatures act as one-time intermediaries on its behalf, so that the user does not need to compromise the security of their wealth to prove that they have the authority to make a transaction. Public keys, similar to postal addresses, are the “send to” addresses. These public keys are used to record transactions on the prior mentioned public ledger.
When Peter sends bitcoin to Paul, he generates a digital signature with his private key from the data composing the transaction, so digital signatures are unique and can never be reused. The node network then uses the digital signature to independently verify that the transaction corresponds with Peter´s public key, and the update is applied to the public ledger of each node. Peter´s balance decreases and Paul´s goes up, and the transaction becomes a part of Bitcoin´s transaction history. Since the digital signature is dependant on the message, nobody can modify the message while passing it along, because any changes invalidate the signature, and the node responsible would be bypassed.
If you´re curious about the math behind all this, investigate trapdoor functions and ECDSA (elliptic curve digital signature algorithm).
A closer look at the ledger
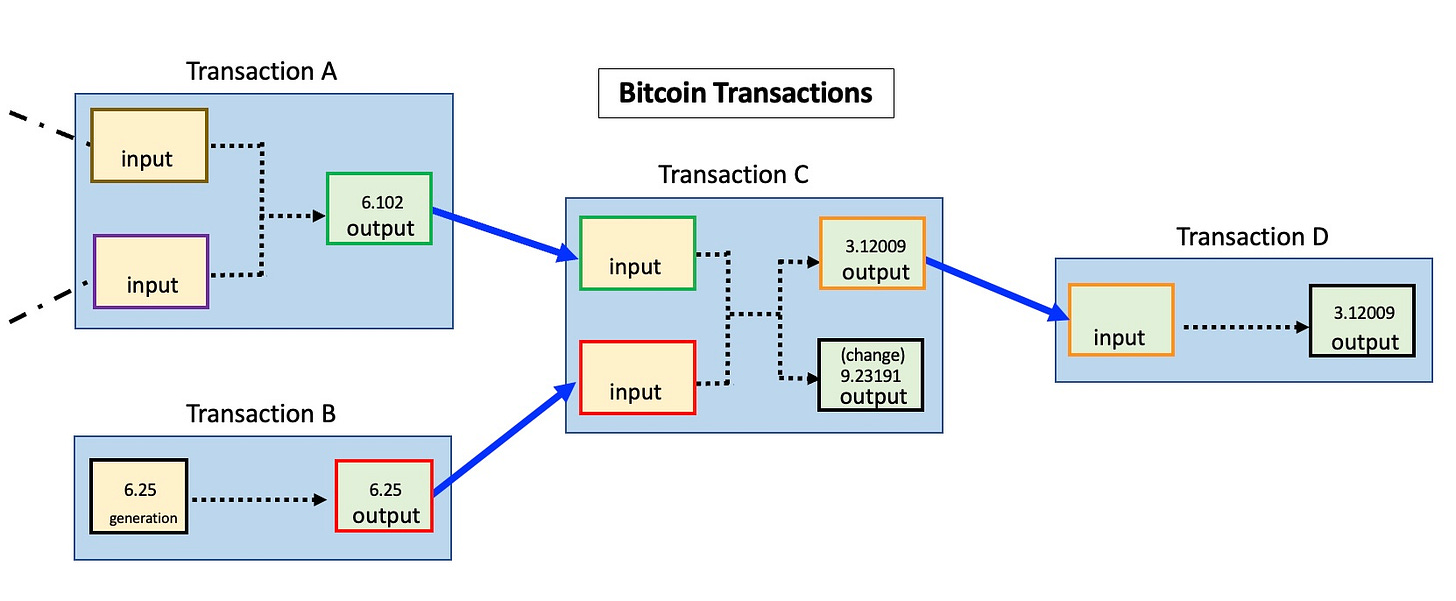
Let us have a closer look at how nodes in the network keep track of account balances. Nodes do not actually store balances of accounts. To verify that a user has sufficient funds to send a transaction, the network needs to reference previous transactions and check to see if the sender had previously received bitcoins in sum greater than or equal to the new transaction. These historical transactions are called inputs. For simplicity sake, all inputs need to be used up completely in a transaction. It is most often the case that an output transaction does not exactly match the input amount, so the sender must send themselves the difference as change.
Through these aforementioned input-output linkages, Bitcoin ownership is passed on down a chain, such that the validity of new transactions is dependent on previous transactions. A break in the chain would invalidate future transactions, which is why Bitcoin wallet software downloads every single transaction dating back to the very first, and checks the validity of each one. This initial verification can take over a day to finish, but it only needs to be done once, and this makes Bitcoin a trustless transaction technology system.
Preventing double spending
Once a transaction has been completed, it is labeled as “spent”, and cannot be used again. Without this rule, someone could double spend an input by referencing it in multiple transactions. This requires that nodes check the inputs of every transaction, to make sure that the bitcoin has not already been spent, and to do this they need to check every transaction ever made. There have been hundreds of millions of Bitcoin transactions, so at a glance this process may appear unrealistically time consuming, but it is all sped up significantly by an index of unspent transactions called the UTXO set (unspent transaction output).
So, instead of keeping a ledger of bitcoin balances, nodes keep track of a giant list of transactions. To word it with technical accuracy, owning bitcoin means that there are transactions recorded in this list which point to your public keys and have not been used in inputs for other transactions. For a user to know their Bitcoin balance, they scan through all of the transactions and total up their unspent inputs.
Complex Transactions
Outputs are more like puzzles than a simple to/from address of an email message. Sending bitcoin is like placing it behind a locked door, and attaching an encryption which needs to be solves in order to access the funds. While typically the conditions to open the box are set so that a single recipient can receive the funds in the aforementioned manner, special conditions can be set by the user, such as escrow transactions for buying property, or to buy or sell Bitcoin on peer-to-peer trading platforms like Hodl Hodl. Bitcoin´s capacity for complex transactions is enabling the development of layer two solutions like Lightning, Liquid, and Fedimint, but today we are focused on Bitcoin Core and will save layer two developments for another day.
The importance of anonymity
As we explored in previous sections, Bitcoin uses a public ledger system. Anonymity is the key piece to maintain transaction privacy. When using Bitcoin, it is advisable to use systems like Tor and anonymous VPN services to avoid linking user identity (or any information that may allude to it) to their bitcoin keys.
Many exchanges today, due to government regulation, require KYC (know your customer) information which frequently includes home address, legal documents, and facial recognition. Once this information is tied to your Bitcoin, it can be monitored and regulated. KYC contaminated Bitcoin can compromise otherwise anonymous bitcoin transactions by the same mechanisms which make Bitcoin transactions trustless and secure. Bitcoin on its own is completely anonymous, and thus private. Our interactions with third party systems are how we compromise that privacy.
This article is intended to provide a birds eye view on how Bitcoin works rather than a step-by-step guide, but in proceeding I implore readers to value the anonymity of their public keys.
Creating new addresses
A user can use their Bitcoin wallet software to randomly generate a new private key and corresponding public key. There are so many possible addresses that there is no need to check if the address is available, since guessing someone else´s private key is virtually impossible.
To get a sense of the odds, here is the total number of possible Bitcoin addresses:
1461501637330902918203684832716283019655932542976
Number of grains of sand on Earth is roughly:
1500000000000000000
Rough total number of existing addresses with a positive balance:
50000000
For this reason, a new Bitcoin address can be generated without an internet connection (enabling 100% offline storage for enhanced security) and the difficulty of stealing someone else´s bitcoin by guessing their private key is so high that it would be far more profitable to mine new Bitcoin instead and help further protect the network from attacks on the blockchain (more on mining rewards, proof-of-work, and blockchain coming up). The astronomical quantity of possible Bitcoin addresses is a big part of what makes Bitcoin so secure.
How Bitcoin solves the transaction order dilemma
Due to the decentralized structure of the Bitcoin network, the developer who operated under the pseudonym Satoshi Nakamoto (Japanese for Central Intelligence) had to come up with a new solution for the major security hole of previous cryptocurrencies; transaction order. Considering how transactions pass node to node through the network, there is no guarantee that the order in which they are received is the order that they were made. A simple time stamp is not sufficient because it could be easily modified.
This dilemma opens up a risk of fraud. For instance, Joe could make a payment to order a product online from Liz, wait for her to ship the product, and then send another transaction referencing the same input to himself. The result would be such that some of the nodes on the network receive the double-spent transaction before the legitimate one, and consider the legitimate payment to Liz invalid for recycling an input. This would cause Liz financial loss, and create catastrophic disagreement across the network, since there would be no way to prove which transaction came first.
With this in mind, it is clear that nodes need to agree on transaction order for Bitcoin to function.
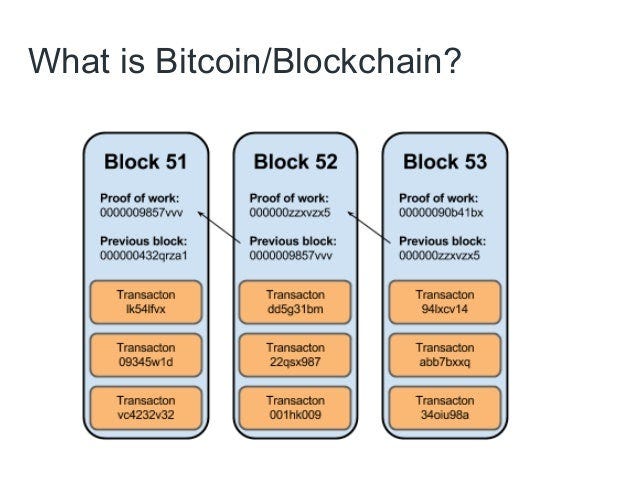
This is where the mastery and intellectual genius of Satoshi Nakamoto was demonstrated. The Block Chain was his ordering solution, which prevents double spending bitcoin through a mathmatical computer race known as proof-of-work. This ordering system groups transactions into what we call “blocks” and links them together in a chain of transactions dating back to Bitcoin´s inception in 2009. Hence the term “blockchain”.
The blockchain is used to order transactions, and the aforementioned transaction chain keeps track of ownership changes. Every single block references the block before it, transactions within the same block are considered to have happened at the same time, and transactions not already in a block are regarded as unconfirmed. All nodes can collect unconfirmed transactions and broadcast them as suggestions to the rest of the network for what the transactions of the next block should be.
How does the network decide which node chooses the next block? Simple. There is a computer race to solve a mathmatical encryption which would take a single machine years to solve, but with the combined computational power of every participant in the world (governed by automatically varying difficulty levels of the encryption), this race is completed every 10 minutes. The winner of the race gets to decide which transactions are included in the next block.
Transaction order vulnerability
Very rarely, a block can be solved at the exact same time by two different entities. In this case, a node simply builds on the block it received first, and other nodes build off of the first one they received. The tie is broken when the next block is solved, because all the nodes immediately switch to the longest version of the blockchain available.
The result is quick stability and final settlement, with all nodes in agreement regarding transactions from blocks a few back in the chain. In the rare cases of block partitions, when the network calibrates to the longest branch, transactions that were in the blocks of abandoned branches will simply go back to the transaction pool in their previous unconfirmed status. Even though the threat is much decreased by transaction ordering with blockchain, the potential for transactions to lose their place creates a small vulnerability for a double spend attack.
Protecting the blockchain with proof-of-work
Solving a block involves trying to get the hash output to be below a certain number, and Bitcoin miners do that by trying different numbers at the end of the block. The hash output then acts as a special fingerprint which uniquely identifies that block. Even if the smallest detail of the block is changed, the hash output would be dramatically different. The hash output is used as the block reference (mentioned earlier) and there is no way to change a block reference in the middle of the chain, because the next block in the chain would not point to it. Furthermore, a future block cannot be solved in advance to the block before it. The previous block reference is part of the text which goes through the hash function of the current block, which is why an attacker cannot premeditatively compute a blockchain partition.
Going back to our double-spending example with this understanding in place, if Joe wants to double spend while purchasing a product from Liz, he would need to compete with the entire Bitcoin network until Liz ships the product hours or even days after the order is made. Joe would need to have full control of the whole electrical grid of Brazil for a 50% chance of solving the next block before someone else, and would need to consecutively win the race until Liz ships the parcel. With access to this much energy and computational power, if it took Liz just 3 hours to ship the package, Joe´s probability of successfully defrauding her would be 0.000381469%.
A miner´s odds of winning the race are equal the percentage of energy and computational power they contribute to the network. Blocks further back in the chain are most secure, and the small double spending vulnerably exists at the end of the blockchain. Therefore, in keeping it trustless, it is recommended to simply wait for a couple of confirmations before considering received bitcoin final.
Where does Bitcoin come from?
As mentioned in the earlier part of this article, to send a bitcoin output, a user needs to reference a previous input to verify that they have sufficient funds to cover the transaction, but where do these coins originally come from and how do they enter circulation? To slowly and randomly distribute bitcoin, a one time reward is given to whoever solves a block. Bitcoin is not backed by a physical commodity, but is rather electrical energy captured into monetary potential energy.
The Halving
Every 210,000 blocks, the reward is cut in half. This works out to be every 4 years, and this event is called The Halving. There is a limited supply of 21 million bitcoin, and in roughly 140 years the last bitcoin will be mined. The halving causes a shift in supply and demand, which causes Bitcoin prices to skyrocket every four years. Because of this, it is a deflationary currency. At my time of writing this, Bitcoin has struck a new all time high in monetary value, in advance to the next halving cycle - less than two months away. A year ago I discussed the implication of The Halving, which you can read here.
Divisibility
A bitcoin is divisible to a hundred-millionth. This smallest unit is called a Satoshi. Even with such a high perceived value, we can transact with small portions of a bitcoin to buy and sell goods from each other, and layer two solutions will benefit from this.
Mining Fees
In addition to block rewards, miners also get to keep any mining fees which can optionally be included with in a transaction. The combination of the growing volume of transactions and the decreasing incentive of block rewards places us in a chapter of Bitcoin´s history when the incentive structure of upholding the transaction order security protocol is shifting towards these mining fees. Additionally, transactors who pay lower fees have their transactions enter the blockchain at a slower pace, and those who do not pay fees rarely get their transactions entered into the blockchain at all. Mining fees have risen substantially in the last few years with Bitcoin´s spike in popularity, and layer two solutions like Bitcoin Lightning are taking the stage for small scale Bitcoin transactions.
In Closing
I hope that this article has provided you with an overview of how Bitcoin works. I hope that you feel a deeper comprehension of what Bitcoin is. I have been approached by many skeptics in the last couple of years since I took a deep interest in Bitcoin, and understand their reluctance to explore this space. The common argument has been that it is the conduit for a CBDC (central bank digital currency), and I hope that this piece has deepened reader understanding of the technology so that their own conclusions may be better informed. In my opinion, Bitcoin is the opposite to a CBDC, and if we can transition to a global condition in which Bitcoin is used as a popular medium of exchange or as a reserve currency, it would become impossible to implement such a centralized system. Most of my previous Bitcoin-related writing has been more philosophically focused, but I think that it is also important to address the technological side of Bitcoin. If you would like to be notified of my upcoming work, which mostly focuses on technological and environmental topics, make sure to subscribe to me here on Substack and follow me on X.
Thanks. I hope you have a wonderful day!







Excellent article that concisely and correctly describes for the general public the genius of BTC.
Thanks Rainn.
There is two items on this, that always is in play, when humans are involved. Use and Ab-use!
When you build a better mouse trap for use. Somewhere a bigger Rat learns to cancel it.
No nations in history have ever "perfected" it's commerce systems from fraudulent practices.
Even trying to turn lead into gold thru creative Alchemy. Money is like a planet Lunar Tide.
Eventually moves to other shores. Raises all ships on one shore and lowers all ships in others.
Bitcoin needs a Gazillion watts of electricity to exist daily. Do you see a problem here? I do.....